Warning! Big Head Ransomware Spreading Through Fake Windows Updates
A malvertising campaign has emerged, distributing a developing ransomware known as Big Head. This malicious software disguises itself as counterfeit Microsoft Windows updates and Word installers. Fortinet FortiGuard Labs recently uncovered various versions of Big Head ransomware that encrypt files on victims' computers and demand cryptocurrency payments in return.
During their investigation, Fortinet researchers noted one variant of Big Head ransomware that presents a phony Windows Update, indicating that the ransomware may have been distributed under the guise of a fake update. Another variant, disguised as counterfeit software, cleverly employs a Microsoft Word icon.
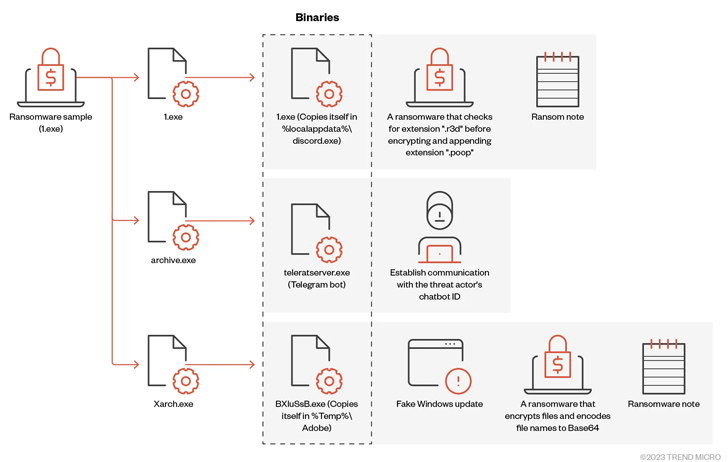
Analysis of this ransomware by Trend Micro revealed its underlying mechanics. Big Head, built on the .NET framework, exhibits the ability to deploy three encrypted binaries. The first, 1.exe, facilitates the propagation of the malware. The second, archive.exe, enables communication through the messaging platform Telegram. Finally, Xarch.exe encrypts the victim's files while displaying a deceptive Windows update.
Big Head ransomware has primarily affected users in the United States, Spain, France, and Turkey. Trend Micro's research sheds light on the deceptive tactics employed by this malware, including the presentation of a phony Windows Update user interface. This interface aims to mislead victims by mimicking a legitimate software update process, displaying progress increments of 100 seconds, adding to the illusion of authenticity.
Big Head is no different from other ransomware families in that it deletes backups, terminates several processes, and performs checks to determine if it's running within a virtualized environment before proceeding to encrypt the files.
In addition, the malware disables the Task Manager to prevent users from terminating or investigating its process and aborts itself if the machine's language matches that of Russian, Belarusian, Ukrainian, Kazakh, Kyrgyz, Armenian, Georgian, Tatar, and Uzbek. It also incorporates a self-delete function to erase its presence.
According to Trend Micro, a second artifact associated with Big Head ransomware has been detected, exhibiting both ransomware and stealer behaviors. The stealer component utilizes an open-source tool called WorldWind Stealer to extract various data, including web browser history, directory lists, running processes, product keys, and network information. Additionally, a third variant of Big Head has been uncovered, incorporating a file infector called Neshta.
This enables the ransomware to insert malicious code into executable files on the compromised system. The inclusion of Neshta serves as a camouflage technique for the final Big Head ransomware payload, disguising the malware as a different threat type, such as a virus. This strategy aims to divert security solutions that primarily focus on detecting ransomware, potentially evading detection.
Although the identity of the threat actor responsible for Big Head remains unknown, Trend Micro identified a YouTube channel named "aplikasi premium cuma cuma," indicating a possible Indonesian origin of the adversary.
The researchers emphasized the need for security teams to remain vigilant due to the diverse functionalities of this malware. Its multifaceted nature poses a significant risk once fully operational, making it more challenging to defend against, as each attack vector necessitates separate attention and countermeasures.



No comments: